Wireless automation is an emerging field of research, engineering and industrial development that aims at significant savings in installation times and costs of cabling in automation systems, while providing a new level of flexibility for system design, reconfiguration, and agility. It is applicable to both new automation systems and retrofit applications. The use of wireless technologies is rather common in consumer applications, consider, for example, cellular phones, cordless desktops, etc., but the strict real-timeliness and reliability requirements of automation systems have limited the use of wireless technology in industrial environments. There are, however, a variety of existing industrial applications of Bluetooth, ZigBee and WLAN networks, but very rarely these are used in time-critical applications. The bulletproof wireless technologies are few, and hence the technologies have not yet spread to wide use in industrial automation. The main concerns in this respect are related to the problem of how the reliability and real-timeliness of wireless communications could be guaranteed.Wireless automation considers a wide range of technologies that are used in an automation system to enable wireless communications on one or several levels of the system, including factory, automation system, and field device levels. The wireless communications are used to deliver measurements and control values, device configuration information and other process data between the devices, control rooms and servers. This chapter reviews the wireless automation standards and related technologies, but also certain medium access control (MAC) and routing protocols and control design approaches are discussed that together could solve the problem of achieving a reliably working real-time wireless automation system. We will also consider simulation of wireless automation systems, which is essential for the network and automation system co-design validation, and evaluate some candidate system designs with a suitable simulator. The focus is on the field device level, and hence the technologies used for device to device wireless communication for control purposes are addressed.
The main contributions of this chapter include a review of current technologies used in wireless automation. We also discuss and propose a new MAC and mesh routing protocol (limited broadcast protocol, LBP) to enhance the reliability and real-time performance of wireless automation systems. We will also demonstrate how the modelling and simulation of packet drops could be done and integrated in the co-design procedure of wireless automation systems. Finally, we will investigate some practical control solutions and designs for wireless automation with a full-scale simulator to validate the proposed designs.
Wireless automation
Wireless automation and the related field of wireless sensor networks (WSN) are currently attracting researchers and industry world-wide. The progress of development has emerged into two industrial wireless automation standards, namely WirelessHART (2007) and ISA100.11a (2009). In the current phase, these standards consider mainly monitoring applications without guarantees of real-time performance. However, in automation systems, it is possible to handle the missing data and variable time-delays induced by the somewhat non-deterministic wireless communications by proper design of the system, especially via appropriate control design.The primary benefit of wireless control technology is the reduced installation cost, as a considerable investment is made in the wiring of factories, both financially and in labor (Brooks, 2001). The use of wireless technology is not only a replacement of cables; the benefits go beyond that. With wireless devices, increased flexibility is gained, as sensors can be placed more freely, even on rotating machines. Robustness is increased, as the communication can be done over several paths in a mesh network and failure of cables is eliminated (TSMP, 2010). Finally, there are the opportunities for new applications that are enabled by wireless control. Some existing or emerging applications are remote control of devices, for example cranes or dexterous and mobile robots, mobile applications, and wireless monitoring of large plants for fault detection, maintenance, production quality monitoring, and compliance to environmental regulations (Gungor & Hancke, 2009).There is a strong aim (Moyne & Tilbury, 2007) to develop and deploy wireless networked control systems (WiNCS), where a control system communicates over a wireless network, in factory and home automation. In a related field, sensor network applications have as well received much attention (Akyildiz et al., 2002; Baronti et al., 2007). Today, wireless automation technologies are mostly used in monitoring applications, because in these applications the operational requirements can be satisfied with the current technology. The industry is cautious in applying wireless to closed-loop control, due to the inherent unreliability of wireless communications. Next we summarize the main research activities on WiNCS to enable wireless automation.
Research on wireless networked control systems
A networked control system (NCS) is a distributed real-time control system consisting of the plant, sensors, controllers, actuators, and a shared data network that is used for communication between the components of the system (Antsaklis & Baillieul, 2004). A general NCS layout is depicted in Fig. 1. In WiNCS, wireless networks are used for transferring data.One of the benefits of NCS is reduced cabling cost (Neumann, 2007), which is removed completely by the introduction of wireless devices. Other advantages include ease of adding field devices, introducing two-way communication with field devices for remote configuration and device health monitoring, and more advanced control strategies are possible because of improved availability of field level data (Gungor & Hancke, 2009; Neumann, 2007). Wireless control systems deliver more benefits than NCSs as there are no wires, but also more problems, mainly because of the unreliable shared communication medium. The main concern against deploying wireless networks for control is the uncertainty of communication and inability to guarantee a sufficient quality of service for the control system. The network must provide real-time and continuous operation, as controlling a physical system is a continuous task (Moyne & Tilbury, 2007). This real- timeliness may not always be guaranteed, which causes problems for the control system design (Lian et al., 2006). Soft real-time operation is enough, if it is taken into account in the control design as shown later on. Another concern hindering the adoption of wireless technologies is security, since the wireless medium is open for eavesdropping and interference (Mustard, 2006). The security issue is solved by authentication and encryption methods (Karlof et al., 2004).
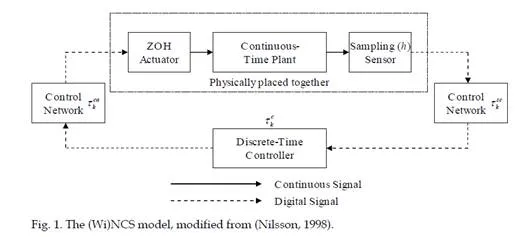
Ethernet networks are becoming regularly used in control applications (Moyne & Tilbury,2007). Similarly the “Industrial Ethernets” (Neumann, 2007), which allow for real-time operation, where an operation is guaranteed to be executed in a given time, are gradually being applied. The same benefits are also available by means of wireless technology, such as WLAN, with the addition of accessing the data wirelessly using a handheld device, enabling in-situ inspection of the process (Brooks, 2001). An overview of NCSs can be found in (Antsaklis & Baillieul, 2004) and (Hespanha et al., 2006). The field of WiNCS is multidisciplinary: the network, the control system and their interactions need to be taken into account. Traditionally, either the network or the control system has been studied separately. As such there has been relatively little research focusing on both aspects at the same time. Current wireless control system research has its roots in networked control system theory, as the issues of a shared communication medium are the same, mainly related to variable communication time-delays and packet losses, and system architecture design, see (Willig, 2008). Both fields deal with network protocols (Akkaya & Younis, 2005; Marco et al., 2010), transmission scheduling (Weiss et al. 2009), communication and control co-scheduling (Samii et al., 2009), traffic reduction (Lian et al.,2002), congestion control (Velasco et al., 2004), estimation (Nebot et al., 1999), LQG control with packet drop (Gupta et al., 2007), Kalman filtering (Sinopoli et al., 2004), controller tuning (Eriksson, 2008), control performance (Lian et al., 2001), and control stability (Cervin et al., 2004; Gupta et al., 2007; Kao & Lincoln, 2004; Weiss et al., 2009). The main difference between NCSs and WiNCSs is that wireless communication is less deterministic because of interference and finite communication range, but problems with wiring and failing connectors are eliminated.
Technologies in wireless automation–A review
The physical properties of the radio, such as frequency, antenna and modulation, determine the range and bit rate of the network. The medium access control (MAC) determines the delay a message experiences before the transmitter gains access to the wireless medium and the message can be transmitted. In a large control system, there are many small packets, containing, for instance, measurements from a sensor or control values to actuators, to be transmitted in a short timeframe. The particular communication attributes and the need for a real-time WiNCS set special requirements on the MAC protocol, which among other things, affects the packet delay and collision probability. The MAC protocol is thus one of the most important network design issues in WiNCS.
Medium access and networking protocol
The main categorization of MAC protocols is between deterministic (contention free) and random access (contention based). In random access MACs, no guarantees that a certain node gets access to the medium in a given time can, in general, be given. Most of the random access MACs used in wireless sensor networks are based on the carrier sense multiple access (CSMA) protocol. In deterministic MACs, a communication slot (either in frequency, time or with code division, or a combination of them) is assigned to each node. This assignment has the advantage that the communication is deterministic in the sense that the access to the medium can be guaranteed in a predetermined time. Networks using time- scheduled MAC are typically controlled by a centralized network manager, and they require tight time-synchronization of the whole network. The advantage of random access MAC is that in low traffic conditions (low sampling rate), any node can transmit immediately if the medium is idle. In high traffic conditions (large number of control loops or high sampling frequency), a packet might experience collisions and random back-off times. The non-deterministic exponential back-off is not suitable for wireless control applications, since the communication delay, which is important for the control stability (Cervin et al., 2004), cannot be bounded and packet drop due to congestion decreases the performance (Liu & Goldsmith, 2003). Therefore, deterministic MAC protocols are often desired in control applications to overcome the problem of variability in transmission times. Although deterministic MAC protocols might not always provide the optimal use of resources, they are used in WiNCS as one solution to support real-timeliness. In current wireless automation standards, the trend is also to use deterministic MAC protocols, which enable a reliable communication schedule for periodic measurements and control packets.
The original IEEE 802.15.4 standard defines two operation modes. In the beacon mode, it is possible to utilize both reserved time slots (scheduled MAC), and contention based slots (random access). However, most of the shipped radios nowadays come only with CSMA random access MAC, which is due to the complexity of the beacon mode protocol and its known performance problems (Werb et al., 2005). The WirelessHART protocol (WirelessHART, 2010), aimed at industrial applications, defines both token passing and scheduled MAC. The protocol allows frequency-time slots to be dedicated to links. Some slots can also be reserved for contention based access using CSMA. Another industrial wireless automation standard is ISA100.11a, which uses a similar MAC protocol to WirelessHART. These industrial standards are further discussed in Section 3.As in any realistic large-scale sensor network, not all the nodes are able to communicate directly with each other due to the limited radio range and dynamic nature and other challenges posed by the environment. Hence routing protocols are needed to ensure that the data could be transmitted from any node to any other node at all times in the network. The aim of a routing protocol is to setup the routes in the network in an energy-efficient manner and to reliably relay the data from the source to the sink node (Akkaya & Younis, 2005). Typically in monitoring applications, the data are eventually collected into one of the nodes, i.e. the sink node, having the capability to store the data for offline analysis and/or visualize the data for the system user.Many of the proposed routing protocols can be divided into data-centric, hierarchical or location-based, but some of them also consider e.g. network quality of service (QoS). For a more detailed review of routing protocols in WSN, see (Akkaya & Younis, 2005). It should be noticed that especially in networks having real-timeliness constraints, the MAC and routing protocols are tightly coupled. For example, an intermediate node on the route should be able to forward a message once the node receives it as fast as possible to the next node along the path to reduce the end-to-end communication delay. In WirelessHART networks the routes are either predetermined by the network manager (graph routing) or determined by the nodes themselves (source routing for ad hoc communications) (Song et al., 2008).
Radios for wireless automation
Wireless networks for control applications are currently envisioned to use existing standard wireless technologies, such as Bluetooth, ZigBee (based on IEEE 802.15.4 radio) (Baronti et al., 2007), and WLAN (IEEE 802.11). Nevertheless, it should be noted that the traditional computer networks, such as Ethernet and WLAN, use CSMA type medium access control with exponential back-off in case of collisions, which is not always applicable in wireless control as already discussed above. The wireless network design problems are further discussed, for instance, in (Kumar, 2001).Wireless networks are already used in control. The preferred solution is to use deterministic networks, using polling (e.g. Bluetooth) or scheduling (WirelessHART and ISA100.11a), but standard wireless networks are also used in control applications. Using standard wireless hardware for automation is considered in (Pellegrini et al., 2006), where two application layer protocols suitable for real-time control are designed and evaluated. Some early adoptions of wireless devices as cable replacements are listed in (Koumpis et al., 2005). The first wireless deployments have been mostly cable replacements using Bluetooth. Bluetooth has, however, given way to ZigBee, as ZigBee has lower power consumption and more flexible networking.
An overview of ZigBee/IEEE 802.15.4 can be found in (Baronti et al., 2007). ZigBee has rightfully been criticized for being unreliable, lacking techniques to mitigate the communication problems, and unsuitable for industrial control (Lennvall et al., 2008). ZigBee is more suitable for small applications, and there are separate industrial standards for wireless automation. ZigBee is used, for example, for home and building automation as an enabling technology to create smart home and smart energy applications. WLAN networks provide such high data throughputs that they could be well used in automation systems from the data rate point of view. The problem with WLAN is the high energy consumption of the radio. Obviously, a standard WLAN network does not support real-time communications, but the radio technology itself is useful for creating high-bandwidth real-time systems. Nevertheless, it is challenging to create purely wireless WLAN networks for automation due to the high energy consumption of the nodes. For cable replacement, though, if power is available from the process, the WLAN radios can be well used for single hop wireless communication.
The use of heterogeneous networks spanning the whole automation system from low level devices to high level functions, such as production monitoring, is considered in (Moyne & Tilbury, 2007; Neumann, 2007), where the applicability of different networks at the different levels and tasks are evaluated. For the higher level functions, such as plant monitoring and production planning, trend analysis, or gathering of batch information, real-time operation is not necessary, and office grade wireless networks are suitable for these tasks. In the current wireless automation standards only field device level wireless networks, where sensor devices report their measured values and possible health data to a gateway and the rest of the automation system, are considered. The network is thus used only at the lowest device level in the whole automation system (Steigmann & Endresen, 2006). In practice, also plant wide wireless networks with proprietary protocols based on the office grade IEEE 802.11 standard are used.
Standards and applications
Currently, there are two standards for industrial wireless automation: WirelessHART and ISA100.11a. Both industrial standards are based on the IEEE 802.15.4 radio (ZigBee, 2006). The IEEE 802.15.4 standard is suitable for building automation (Kintner-Meyer, 2005), industrial monitoring, and control applications (Wheeler, 2007). The main characteristics are low bit rate and low power consumption. The WirelessHART standard and some implementation details are discussed in (Song et al., 2008). ISA100.11a is in practice very similar to WirelessHART, as both have similar design goals, but the two standards are not compatible. Furthermore, it should be noted that the WISA system (Scheible et al., 2007) is a complete solution for a reliable wireless cell in industrial manufacturing.
The architecture of both industrial wireless automation standards includes sensor nodes, wireless routers communicating with each other, and a gateway, which is connected to the automation fieldbus and the rest of the automation system. Mesh networking is possible for reliability, but all communication between devices in the wireless network is routed via the gateway. This routing constraint makes the network scheduling and routing easier. WirelessHART is by now in use (WirelessHART, 2010) and several manufacturers have released devices for WirelessHART. The ISA100.11a standard (ISA100, 2010) was published in September 2009, and is submitted for ANSI and IEC standard approvals. Hence, the field of industrial wireless control has taken its first steps. The standards are designed for determinism, such that traditional control can readily be applied. Although determinism is the main design goal, this is never fully assured. Wireless networks are inherently non- deterministic, and no network design can make it fully dependable, because of interference in the open communication media.
The WirelessHART protocol is designed for deterministic communication and interference resistance, satisfying the real-time requirements of a wireless control system. WirelessHART uses a combination of time division multiple access (TDMA) and frequency division multiple access (FDMA) MAC protocol. The TDMA slot length is 10 ms, in which the data packet with sensor or control information and an acknowledgement are exchanged between two nodes. The network and transport layers are based on the Time Synchronized Mesh
Protocol (TSMP) originally developed by Dust Networks (TSMP, 2010). Each node pair is assigned a unique time/frequency slot for contention free communication by a centralized network manager. Some slots can be reserved for contention based access using CSMA, for communicating rare event messages. Additionally frequency hopping is used to mitigate interference on some channels. A more detailed presentation of WirelessHART can be found in (Song et al., 2008). The benefits of WirelessHART and how to accommodate the control system to the wireless network, and meet the required control performance, is discussed in (Nixon et al., 2008). ISA100.11a uses similar techniques and both network standards can be applied where the application can tolerate a delay jitter in the order of 100 ms. The delay jitter stems from packet drop due to interference. In laboratory setting, the TSMP combined with frequency hopping over the 16 available channels of the IEEE 802.15.4 radio has been reported to achieve carrier grade reliability for a low data rate wireless sensor network (Werb et al.,2005).
Due to the determinism of the TDMA approach with a pre-determined schedule, fixed bounds on the communication can be advertized, although not guaranteed. In the case of packet drops due to interference or fading, retransmission is needed, which may cause the information to exceed the delay bound. Retransmission slots must thus be incorporated into the schedule, which reduces the bandwidth usage and unavoidably introduces delay jitter. Retransmission can take place on the slots allocated for random access, or on extra slots allocated in the schedule. Current research related to the standards is, for instance, communication and controller scheduling (Samii et al., 2009) and the optimality of the time/frequency-slot scheduling and routing (Weiss et al., 2009).Despite the wireless communication, the devices may still have wired power, because of large power requirements of the sensor or, usually, the actuator. For truly wireless devices, the power source must be local. A battery contains a finite amount of energy, and thus either the device lifetime is limited, or energy must be gathered during operation from the environment with energy harvesting techniques. Sources of auxiliary energy are, for example, electromagnetic waves, light, vibration, or temperature differences (Paradiso & Starner, 2005). Another solution to completely get rid of cables is wireless power transportation. An existing solution is inductive power transfer to devices located inside a cage by the ABB WISA system (Scheible et al., 2007). The cage walls induce a rotating magnetic field that solenoids in the devices convert to current. Typical power transfer ranges from 10 to 100 mW (Steigmann & Endresen, 2006).
Design challenges and solutions
The wireless roadmap, with the needed technological and social development for the adoption of wireless technology in automation, is summarized in (Koumpis et al., 2005). A comprehensive overview of current technologies, future issues, and research topics of wireless industrial networking is given in (Gungor & Hancke, 2009) and (Willig, 2008). Several wireless standards are presented and the anticipated promising research topics are introduced. Some of them are: network architecture and scalability, network standards, quality of service measures, provisioning and analysis of wireless industrial networks, real- time and reliability, security, and energy efficiency.There are many other papers giving an overview of the current wireless technologies and networks for control, e.g. (Gungor & Hancke, 2009; Pellegrini et al., 2006), and (Willig et al.,2005). Gungor & Hancke (2009) review the challenges, design goals, and technical solutions for industrial wireless sensor networks. Willig et al. (2005) discuss several properties and challenges of using wireless in real-time control applications. Some of the network related issues are: interference, path loss, timing and timeliness, co-existence of other wireless networks, and connection to an existing wired automation system. Pellegrini (2006) discusses the requirements and features for using wireless at the device level in an automation system, including power consumption, security, and connection to the wired control system. The necessity of wireless protocols aimed specifically at control applications is also pointed out.
Radio environment challenges in wireless automation
The use of wireless technologies in automation also introduces new challenges, as cable replacement does not simply mean unplugging a wire and using a wireless device instead. The radio channel is a shared medium, and thus subject to interference from co-channel transmissions. Wireless communication is usually less reliable than wired solutions. Radio propagation conditions in industrial setting can be harsh. Measurement results in factories indicate that the channel is subject to frequency selective fading due to multipath propagation. Furthermore, errors tend to appear in bursts in which several consecutive packets are lost (Willig & Mitschke, 2006). The unreliability and interference problems of the wireless networks can be addressed in the different protocol layers. These design choices have an impact on the used control methods, which also need to be redesigned to cope with the problems of wireless communication.In the current wireless automation applications, the radios typically operate in the open 2.4 GHz ISM frequency band. The ISM band is quite crowded, as also the office networks (WLAN, Bluetooth) operate at the same frequencies. The existence of other networks in the same band does not mean that the wireless automation network could not be used. The reliability of communications depends then on the activity of the interfering network. To avoid collisions and interference, frequency hopping and channel blacklisting are useful techniques. In the future, a separate frequency band should be reserved world-wide exclusively for industrial automation applications, to enable proper, interference free wireless control operation.
There are several studies of the performance of IEEE 802.11 networks, e.g. (Prasad et al.,2001), where the network design is also discussed. In industrial or factory environments the radio propagation signal deviates considerably from the ideal free space propagation models used in most network simulator models. Besides the free space model there exists many other fading models for wireless communication (Goldsmith, 2004). Metal and obstacles, typically present in a factory, cause shadowing and multipath effects that amplify or attenuate the radio signal strength. The radio environment in a factory can be harsh with motors radiating interfering electromagnetic waves and moving machinery temporarily blocking links of the wireless network. Reflections of radio waves, causing multipath fading, can in these environments be an advantage, because shadowed locations can obtain a strong signal through reflections.
There are some reports on studies of measurements done in industrial environments. The received signal strength in a chemical pulp factory, cable factory and a nuclear power plant was measured with an IEEE 802.11 network at the 2.4 GHz ISM radio band (Kjesbu & Brunsvik, 2000). The conclusions of the experiments were that the radio environment is not as harsh as initially thought; multipath improves the signal strength in shadow areas. While many locations are improved by multipath fading, communication in some locations is impossible, due to no signal or destructive interference, even if the distance is short (Björkbom et al., 2010). Another study presents measurements of the bit-error-rate and more importantly, the error pattern, of an IEEE 802.11 network in an industrial environment (Willig et al., 2002). Interesting findings were that the packet losses are correlated, error burst and packet loss burst lengths fluctuate several orders of magnitude with time. This means that the outages due to consecutive packet drops may be long in some instants and hard to eliminate, for various physical reasons caused by the environment and the radio. On the other hand, error free periods also vary and can be long. Packet loss rates vary from the high 80 % to less than 10 % in generous situations.
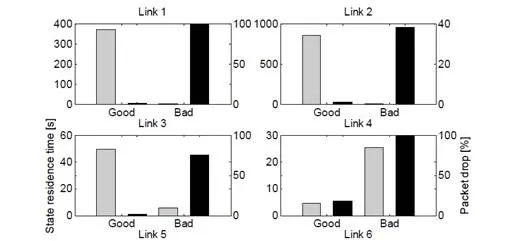
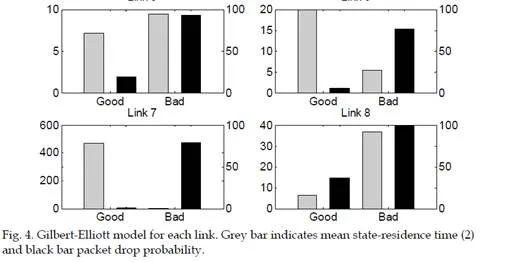
Next, we present a method for modelling packet drop probability in an industrial environment, such that the models could be used in wireless automation network and control design. The measurements done in a real industrial hall show the challenge of wireless communication in harsh environments. When packet drop occurs, feedback information for the controller is not available and the real-time operation of a wireless automation network is endangered. Suitable control design to cope with this problem is presented in Section 5.
Measurements and models for radio environments
In order to study and design WiNCS, realistic packet drop models of networks are needed, since information loss affects the control performance. The physical properties of an existing radio environment can be assessed by carrying out actual measurements at the target site, as described next. Our interest is to use IEEE 802.15.4 radios in a particular industrial environment and hence the tests are performed with such radios. To efficiently collect packet drop data from an environment of interest, we propose the following hardware setup to be used for the tests. The transmitter device is connected to two monopole WLAN antennas, with a spatial separation of 12.5 cm. Similarly four receivers are arranged in an array, placed 6.25 cm from each other, which is half the wavelength at 2.4 GHz. The purpose of having multiple antennas at the transmitter and receiver is to implement and test diversity techniques (both temporal and spatial diversity).The sensor nodes are equipped with Texas Instruments CC2431 radio modules. Transmission power is set to 0 dBm and measurements are taken for several different distances and locations. The transmitter switches between the two antennas for every consecutive packet, thus eight different signal paths are recorded. A total of 15000 packets of size 119 bytes are transmitted for each location at an interval of 0.1 seconds. In the tests, we use the channel 26 of the IEEE 802.15.4 radio, which has the least frequency overlap with the IEEE 802.11 radio, to mitigate packet drop due to WLAN interference and other devices. Packets are recorded with their RSSI value (Received Signal Strength Indicator) and an indication if the packet was correctly received with no bit errors, or dropped. These measurements differ from other similar measurements, e.g. (Kjesbu & Brunsvik, 2000), as the packet reception is measured, not only the received signal strength. Here, the same hardware as would be used in a real application is used, not a specialized measurement device, which could differ significantly from the signal reception capabilities of the actual device.
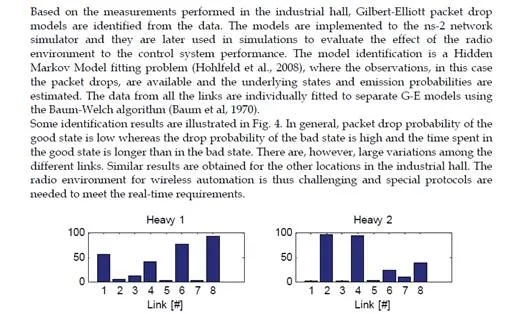
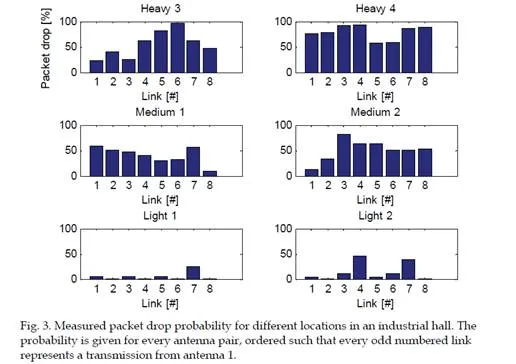
As an example, measurements performed in an industrial assembly hall are presented. In the industrial hall there are machines, racks of tools, and open spaces. Measurements are made in different parts of the hall, which can be categorized as light: open space, medium: mostly open with machines standing on the floor, and heavy: racks of tools obstructing the line-of-sight. The distances between the transmitter and receiver for the different measurements are in the range of 25-35 m.
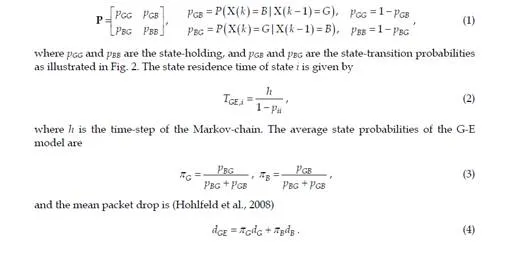
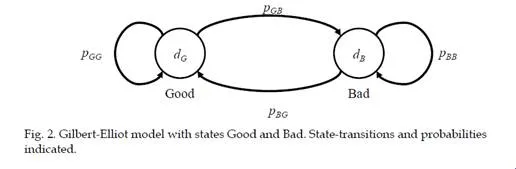
The packet drop results from the industrial hall case are shown in Fig. 3. The packet drop probability varies from location to location and there is significant variation between the antenna pairs. This implies that the signal strength is very sensitive to the antenna location, due to multipath fading.A common way to model a network with packet drops is the Gilbert-Elliott (G-E) model (Elliott, 1963; Gilbert, 1960), which is based on the Markov-chain. The G-E model has two states: one corresponding to good (G) and the other to bad (B) conditions, with separate packet drop probabilities in the good and bad state,
P(drop|G) = dG
and
P(drop|B) = dB , respectively. The transitions between the states follow a two-state Markov model. The state- transition matrix is given by
Enhancements to MAC and routing protocols for real-time communication
There are several methods to design the network protocols such that real-time requirements of the control application can be met. In general, to enable real-time operation, the handling of packet drop should be such that the retransmission has the highest probability to succeed. This is achieved with diversity: if the packet drop was caused by interference, it is likely that interference will continue and therefore retransmission is wise to do on another frequency. In general, the following diversity methods are available: frequency (channel hopping), time (retransmission), code, spatial (send to different node or with different antenna), which all should be optimally used.
Reliability and real-timeliness of wireless communication can be improved in many ways.Reliable hardware with powerful enough radio is the base for all wireless technology. However, reliable hardware itself does not guarantee reliable nor real-time communication,
and instead the communication must be controlled and organized for optimal performance. The interest in using wireless sensor networks for real-time applications, such as process control, has grown during the recent years. Therefore, considerable research effort has been put into developing reliable real-time routing protocols, which also consider the computational limitations and energy constraints of the wireless devices. Some protocols, such as SPEED (He et al., 2003) and MM-SPEED (Felemban et al., 2006), are based on geographic routing mechanism. Both the protocols rely on position information of the nodes, which they receive via GPS. Optimal route is determined based on the distance between the source and destination and the time left to deliver the packet. In indoor situations, the location information should obviously be obtained by other means than the GPS. RTLD (Adel & Norsheila, 2008) takes a similar approach, but the localization of the nodes is done based on the RSSI-values and a path loss model of the environment. Yet, another similar protocol is proposed in (Abinash et al., 2006), the main difference being a prioritized MAC, where real-time packets have shorter backoffs and inter frame spaces (IFS) than other packets. Real-time and non-real-time packets also have different transmission queues and the real-time packets are sorted by an urgency factor.
These sorts of solutions are suitable for large scale WSN, where the nodes are spread over a large area and distances between the nodes are long.Another way to approach the problem is to make modifications on the MAC layer. Black Burst (BB) contention has been studied in (Sheu et al., 2004; Sobrinho & Krishnakumar,1999). In BB contention the nodes jam the channel with pulses of energy, the duration of the pulse is relative to the time the nodes have been waiting for the access to the channel. The node which has been waiting for the longest time transmits a longer pulse than any of the other nodes and thus gains access to the channel. In (Sheu et al., 2004), additional modifications have been made to the MAC to deal with situations where several nodes have packets with same priority. After the BB contention a unique ID is given to each node and then the nodes transmit in a round robin manner based on the IDs. This sort of solution can be easily implemented on top of CSMA by substituting random backoffs with BB. However, the downside is that both energy and time are wasted for contending over the channel. Both ODMRP (Lee et al., 2002) and AMRoute (Xie et al., 2002) take advantage of a multicast scheme. They are designed to be robust and reliable communication protocols for wireless ad hoc networks. In addition to multicast communication, both protocols utilize a mesh topology instead of a conventional tree type of network for improved reliability. Improved reliability is a result from the fact that even if the network topology changes, a mesh is more likely going to maintain some functional links between the nodes unlike a tree, where even one broken link will obstruct the communication. However, neither of the two protocols focuses on the network latency or real-timeliness and is therefore not suitable for control applications. Since wireless control networks are typically limited in the number of nodes and the amount of data needed to be transmitted, the communication protocols need not to be ultimately scalable nor support high data rates. From this perspective, we have developed a robust communication protocol for real-time control applications called Limited Broadcast Protocol, which will be presented next. It has been implemented and tested on IEEE 802.15.4 compatible wireless sensor nodes, but it could also be applied on different radio network platforms after some adjustment of communication parameters.
Limited Broadcast Protocol
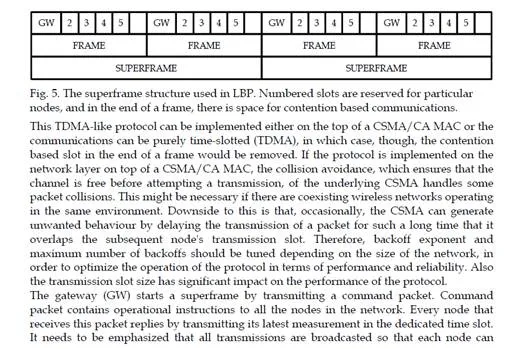
Limited Broadcast Protocol (LBP) is a wireless communication protocol designed for real- time control applications with limited size networks. It is designed for a scenario, where the gateway needs to repeatedly collect new measurements from the nodes of a sensor network in a predefined time, which could be in the order of 50-500 ms. LBP takes advantage of mesh networking and broadcasting. In a dynamic environment a mesh network is relatively robust, since there could be several links between the different nodes. If one link fails then alternative routes can be used for delivering packets with minimal additional delay. All transmissions in LBP are broadcasted and in an ideal case every node is capable of receiving and forwarding any packet in the network. In this way, occasional link failures do not deteriorate the performance of the network. To meet the real-time requirements all transmissions are scheduled in time in order to avoid packet collisions and unnecessary retransmissions. Reliability is achieved by a smart retransmission system in addition to packet forwarding, piggybacking and multi-hop communication. The protocol uses dedicated time slots for communication (i.e., TDMA). All communications between the nodes occur during a superframe (Fig. 5). The length of the superframe is determined by the maximum delay that can be tolerated in the system, i.e. the time in which all sensor values need to be collected by the gateway node. The superframe further consists of several repeating frames. Consequently, the length of a frame is determined by the number of nodes in the network and the length of the slot reserved for each of them. At the end of each frame, one extra slot is reserved for receiving late replies possibly generated by the CSMA as described below. A frame is repeated, within a superframe, as many times as necessary to receive a reply from all the nodes. However, if a superframe expires before all nodes have replied, there will be no more retransmissions and the data are lost. When all the nodes have replied a new superframe can be initiated.
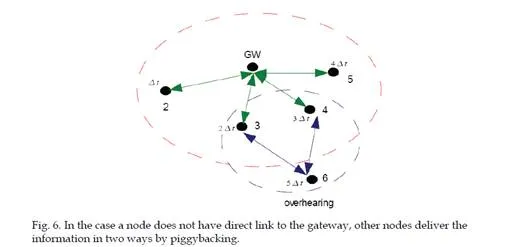
receive all the information available in the network. Thus within the limits of maximum packet size, all available data that have not yet reached the gateway can be forwarded in the same packet by any node. This type of packet will be referred to as a status packet. If a node misses the first command packet from the gateway then any of the received status packets can be used as a reference (Fig. 6). All the replies are scheduled in time in order to minimize the possibility of collisions and the resultant packet drops. A node, including the gateway, is always either in receiving state or transmitting a packet. This ensures that critical data are not lost unless there are serious connectivity problems. The final time slot in each frame is reserved for contention based communications. This slot can be used by a node that has missed its own time slot during the frame, e.g., if it has no direct link to the gateway. Such nodes may transmit in this slot, and hence they do not need to wait for the next frame and their own slot in that.
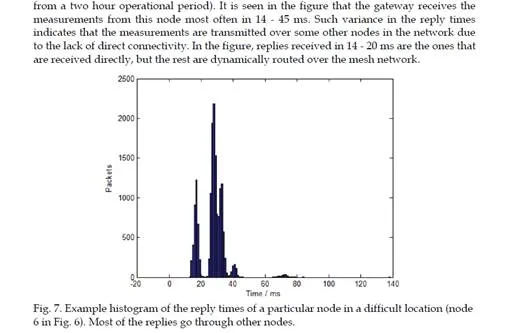
During the test period, the protocol was run for approximately 750000 superframes. The gateway was able to receive the measurements from all the nodes in >99.91 % of the cases in <100 ms. Furthermore, it could receive all the data in >99.96 % of the cases in <500 ms. During the whole test period, over 6 % of all measurements from one of the nodes were transmitted through other nodes because of the lack of direct connectivity. Clearly the proposed protocol contributes to the reliability and real-timeliness required in wireless control systems, but further developments, such as integration of temporal, frequency and spatial diversity techniques, are needed to attain 100 % reliability.
Control design for wireless automation
Because of the networking challenges described previously, wireless real-time control is not straight-forward. In this section we describe some methods to compensate for the deficiencies of the network at the control layer. The main problem is to guarantee stability of the control system, even if the real-time operation of the network is occasionally compromised. The schedule and retransmissions of the network used in wireless automation determine when information is available to the control system, and hence affect the control operation. There exists work where the actual network MAC protocol and related functions such as duty-cycle (Marco et al., 2010), or routing and schedule (Samii et al., 2009; Weiss et al., 2009) are taken into account in the control stability proof. These rely on a predetermined schedule, whereupon the controller stability is proven. Wireless communication is to some degree
stochastic, so control stability proofs for randomly varying feedback delay are needed, such as the jitter margin presented next.
Jittermargin
Control with packet drops and varying delay stemming from a network is a complex case to be analyzed, because of the stochastic and time-varying nature of the problem. Ensuring stability of NCS has been under much research lately (Hespanha et al., 2006). Some results deal with optimal control (Lincoln & Bernhardsson, 2000), jump-linear Markov models (Xiao et al., 2000) and the jitter margin (Cervin et al., 2004; Kao & Lincoln, 2004). The jitter margin defines the amount of additional delay that a control system can tolerate without becoming unstable. The delay may vary in any way, provided that it is bounded by the jitter margin δmax. By selecting a tuning of a conventional controller such that the control loop has a positive jitter margin, the control loop is stable for network induced delay jitter and packet drop given by the jitter margin. The jitter margin theorem states that in the continuous-time case, the closed-loop system
with process G(s) and controller Gc(s) is stable for any additional delay 0 ≤ δ (t) ≤ δmax in the loop, if (Kao & Lincoln, 2004)
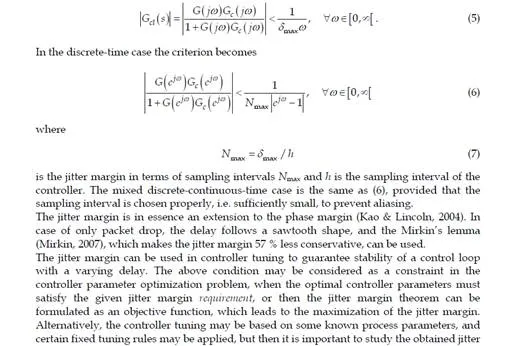
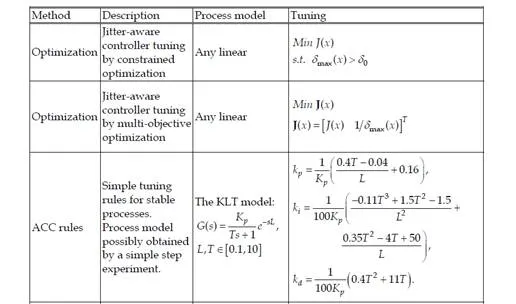
The jitter margin can be used in controller tuning to guarantee stability of a control loop with a varying delay. The above condition may be considered as a constraint in the controller parameter optimization problem, when the optimal controller parameters must satisfy the given jitter margin requirement, or then the jitter margin theorem can be formulated as an objective function, which leads to the maximization of the jitter margin. Alternatively, the controller tuning may be based on some known process parameters, and certain fixed tuning rules may be applied, but then it is important to study the obtained jitter margin with the specific tuning. Examples of such tuning rules and methods for the widely used PID controller are given in Table 1, based on the work in (Eriksson, 2008). It should be noted that many of these tuning rules and methods have the preferred property that the
desired jitter margin is an input to the rules. The tuning adapts the PID gains to ensure a stable control system with individual packet drops, as far as the length of losses is less than δmax . By increasing the jitter margin, the control becomes generally more conservative. The
tuning rules allow the delay to vary in any way, which might introduce some conservativeness to the control design.
Co-design validation by simulation
In addition to the theoretical results, the simulation of WiNCSs is important and necessary for several reasons. Little is said in the literature about the practical implementation, behaviour, and performance of the wireless control systems. Simulations are a feasible way to test and evaluate the practical benefits of the developed theory and algorithms, where the critical properties and behavior of the network, and the impact on the control system can be analyzed. These issues, in particular the protocol specific ones, are hard to approach analytically. Simulation studies will, hopefully, unravel these matters and lead to a coherent theory, best practices knowledge, and design expertise of WiNCSs. To enable the simulation study of WiNCS, the network and control co-simulator PiccSIM has been developed. In the following section PiccSIM is described in more detail and some simulation cases are presented, that show the capabilities of PiccSIM and the benefits of co-simulation for WiNCSs design. The simulation cases involve multiple control loops, which cannot be studied without co-simulation.
PiccSIM
PiccSIM stands for Platform for integrated communications and control design, simulation, implementation and modelling (Nethi et al., 2007) and is developed at Aalto University School of Science and Technology (PiccSIM, 2010). PiccSIM integrates two simulators to achieve an accurate and versatile simulation system at both the communication and control level for WiNCSs. It has the unique feature of delivering a whole chain of tools for network and control modelling and design, integrated into one package with communication and control co- simulation capabilities (Kohtamäki et al., 2009). The tools in PiccSIM range from the design of the system, through simulation and system testing, to implementation of a wireless control system. The PiccSIM simulator is an integration of Matlab/Simulink where the dynamic system is simulated, including the control system, and ns-2 (ns-2, 2010) where the network simulation is done. The PiccSIM Toolchain (Kohtamäki et al., 2009), is a graphical user interface for network and control design, realised in Matlab. It is a front-end for the PiccSIM simulator and delivers the user access to all the PiccSIM modelling, simulation and implementation tools.There are several reasons to build a co-simulation platform consisting of Matlab and ns-2. Matlab and Simulink are widely employed research tools used in dynamic system simulation, providing efficient tools for control design. Control engineers are accustomed to working in this environment. Ns-2, on the other hand, is the de facto standard tool for network simulation in the communication research community. Ns-2 simulates the network on a per packet basis, with models for physical layer, MAC, routing and transport protocols.

Picc SIMarchitecture
The PiccSIM simulator consists basically of two computers on a local area network (LAN): the Simulink computer for system simulation, including plant dynamics, signal processing and control algorithms, and the ns-2 computer for network simulation. For further details see (Nethi et al., 2007), where the integration of ns-2 and Simulink is reported, and (Kohtamäki et al., 2009; Pohjola et al., 2005).
Packets sent over the simulated network are routed through the ns-2 computer, which simulates the network in ns-2 according to any TCL script specification generated automatically by a network configuration tool. Simulation time-synchronization is performed between the computers. To close the gap between the simulators, a data exchange mechanism is implemented, which can pass information from one simulator to the other. This enables the simulation of cross-layer protocols that take advantage of information from the other application layers. An example where the data exchange mechanism can be used is with mobile scenarios, where the location of the nodes and further the network topology depends on the application operation, for instance, in applications of robotics and moving machinery.
Crane control simulation case
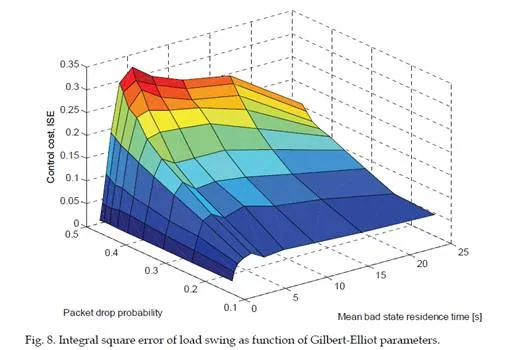
In this section the communication and control co-simulation is demonstrated with PiccSIM, where the impact of the network protocol on the control performance is shown. The benefits of the LBP protocol presented above are demonstrated in a real-time control case, where we simulate an operator driving a trolley crane. The operator gives the velocity reference for the crane with a wireless handheld device. The control messages are routed over a local wireless IEEE 802.15.4 network installed on the crane. The laboratory scale crane model presented in (Eriksson et al., 2006) is scaled up by a factor of ten and used in the simulation cases. The crane control system consists of PID controllers for the trolley and hoist motors, which operate the actuators based on the velocity reference given by the operator through the wireless handheld device. For simulation purposes the operator is represented by PID controllers for the vertical and horizontal movement of the load. For load swing compensation, the human transfer function identified in (Tervo et al.,2009) is used. The load of the crane is moved according to a predefined trajectory, given as reference to the “operator controllers”. In the case of packet drop, the velocity reference is set to zero at the receiving side. The above presented Gilbert-Elliot packet drop models that have been identified based on extensive tests in a real industrial hall are used in the simulations. To assess the impact of the network QoS on the control performance, simulations with different network QoS parameters are made. Several load movement trajectories are simulated with different Gilbert-Elliott network model parameters. The resulting control performances, each averaged over ten runs, are shown in Fig. 8. Obviously, at high packet drop rates the control performance is significantly decreased, but the results also show that it is extremely difficult to predict the effects of packet drops on the control performance without extensive simulations that include the network and dynamical system models.
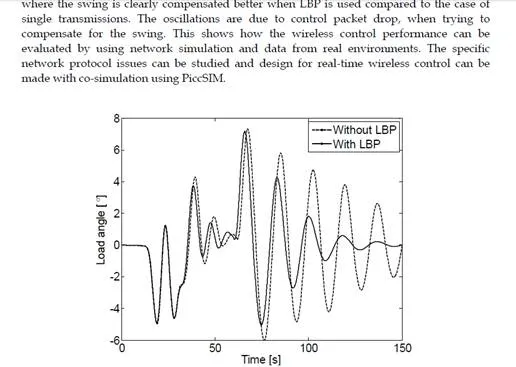
Conclusions
In this chapter, we have discussed the different technologies and methodologies enabling reliable and real-time wireless automation. The industrial environment is difficult for the use of wireless technologies, but there are currently many serious efforts in trying to achieve the level of reliability of wired communications by wireless networks. Some of these efforts have emerged recently into standards of wireless automation, e.g. WirelessHART and ISA100.11a. Besides the technology review, we proposed a communication protocol LBP for real-time networking in limited size wireless networks. The protocol can effectively take advantage of mesh networking and hence change the routing dynamically upon link failures. This is a prerequisite when operating in harsh industrial environments with real- time applications. In the end of the chapter, we presented the PiccSIM co-simulation platform and demonstrated the benefits and capabilities of such a simulator. In WiNCS, analytical results are rarely available regarding the stability of a large-scale system and hence co-simulation may reveal the problems in the design of either networking or control. Furthermore, via simulation greater insight into the behaviour and interactions of communications and control could be obtained.